
Get your free Azure architecture assessment
Do you want to get an independent review of the architecture of your workload? We can provide exactly that!
Based on Microsoft's Well-Architected Framework, we will review your workload based on five pillars and provide you with a list of improvements and recommendations.
Book a free 3-day assessment and we will get in touch with you shortly.
Azure Well-Architected Framework: 3-Day Assessment
This Well-Architected assessment provides insights into how you can optimize your architecture to improve security, reliability, performance and operational excellence in a cost efficient way.
The Azure Well-Architected Framework (WAF) is a set of guiding tenets that can be used to improve the quality of a workload or application. The framework consists of five pillars of architecture excellence: Cost Optimization, Operational Excellence, Performance Efficiency, Reliability, and Security. Incorporating these pillars helps produce high-quality, stable, and efficient cloud architectures.
During the assessment, we will go through these five pillars. Below you can find a short description for each pillar.
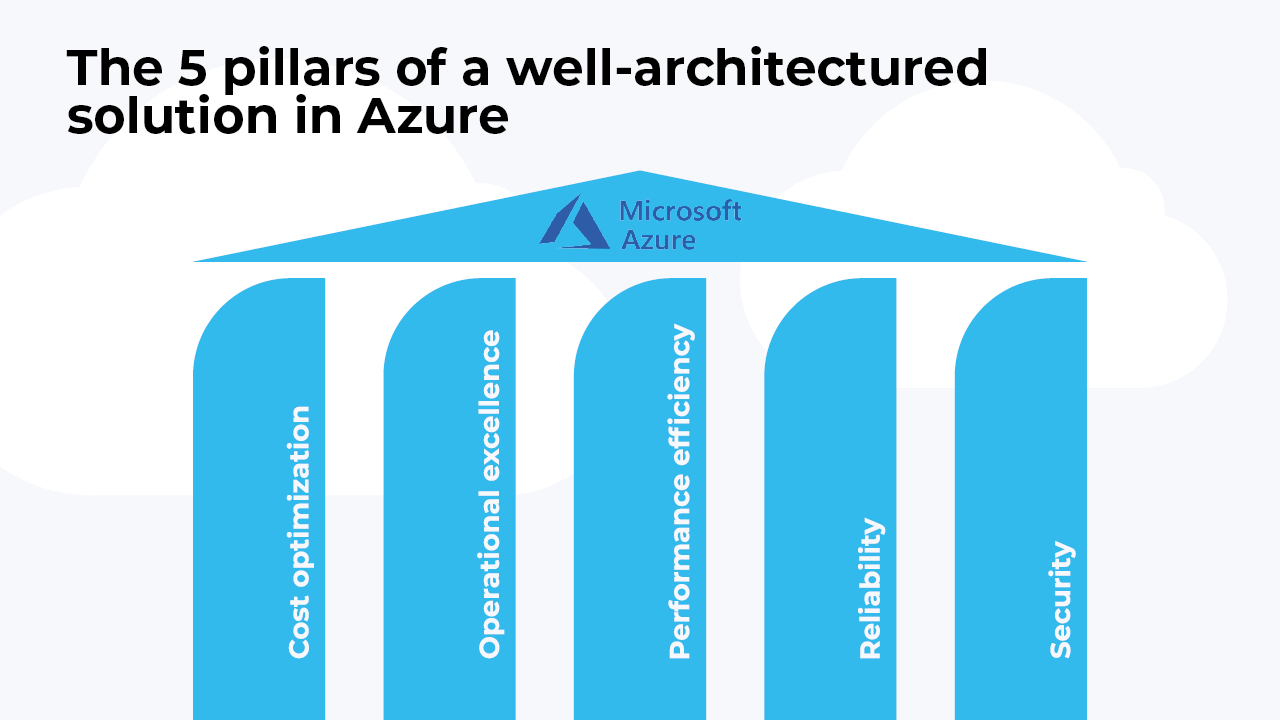
Cost Optimization
Avoid unneeded costs and use the Azure resources in an optimal way.
Operational Excellence
Ensure that monitoring is available on Azure resources and your application. Foresee procedures to resolve issues that might arise and automate as much as possible to ensure reliability and predictability.
Performance Efficiency
Ensure that your application can scale up and down to meet the demand and identify potential bottlenecks. Use the available Azure features to configure the scaling or use high-level (PaaS, Serverless) services to offload the scaling to Azure.
Reliability
Ensure that your application can recover from failures and continue to function.
Security
Ensure that all parts of the system are set up in a secure way. Use identity management to limit user access to subscriptions and resource groups. Verify that your applications are free of any vulnerabilities. Use encryption in transit and at rest to protect sensitive data.